Yesterday (7th Jan 2020) we received information from from the headquarters in Paris about the potential threat to PrestaShop stores. Malicious software is called XsamXadoo Bot and can be used to take control of the store.
Please be advised that all our clients are currently notified of the problem and appropriate actions are being taken. To check and fix the problem yourself, the following steps to take are recommended. Note: You perform all the actions described below at your own risk. If you have any doubts, it is better to seek the help of a specialist.
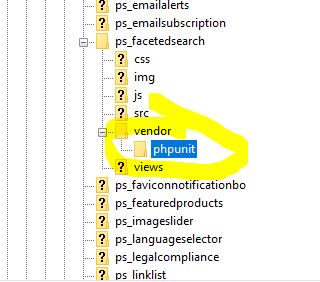
The XsamXadoo bot uploads unwanted files in two locations:
-/vendor
-/modules/<any_module>/vendor
The first (faster) method of deleting files is to execute the following command in the store directory (bash):
find . -type d -name "phpunit" -exec rm -rf {} \;
The command searches for directories with the name 'phpunit' and deletes them along with the content from the server.
An alternative and simpler solution is to manually check the directories mentioned above. To do this, log in through the ftp client, and then you need to browse the above directories (you must view each module directory separately). 
If the 'phpunit' subdirectories are in the 'vendor' directories, they should be deleted.
Note, there are modules in the network that perform these tasks automatically. You can use them, but it's still worth checking mentioned directories by the ftp / bash client.
You must also update the modules to the latest version.
If you suspect that your PrestaShop store has been attacked, then the initial diagnosis can be made in the administrative panel of the store in the location: Advanced → Information → List of changed files (at the bottom of the screen). Unfortunately, there is no 100% certainty that the list is complete. Therefore, if you have any doubts, carefully look through the catalogs of the store, and the code that might be suspicious.
If new important information appears, we will inform you about it. For more information, please visit this page.